What are reverge collectors?
Collectors serve as the distributed job engine for the reverge platform. Operating as a remote collection agent, it receives scanning tasks from the reverge server and executes various tools. This client-server architecture enables scalable reconnaissance operations across multiple environments while maintaining centralized coordination and data aggregation.
The reverge wiki provides documentation for managing collectors on the server side, while the client-side code and documentation are maintained in the open-source reverge collector repository on GitHub. This structure was intentional, allowing the community to contribute by building and integrating additional tools into the project.
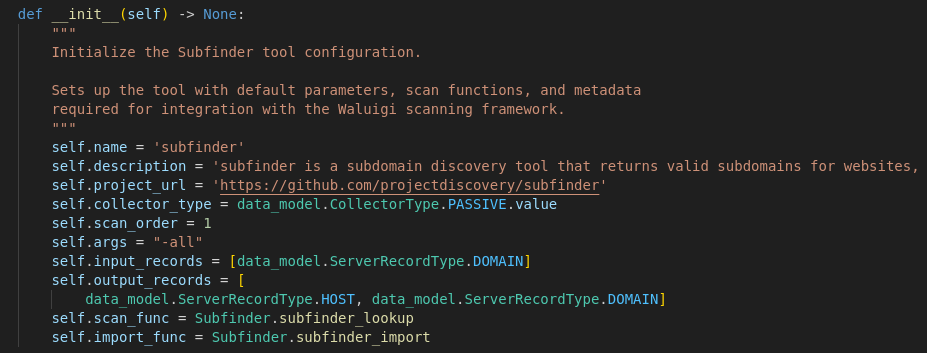
To enable this, a standardized data model was created to define the types of objects a reverge collector tool can generate. Contributors only need to focus on three tasks: translating the scope into inputs a tool expects, executing the tool, and converting its output into reverge data objects. From there, the reverge collector framework handles chaining multiple tools together and transporting the results back to the reverge server. Contributors must also provide basic metadata about the tool, which the Reverge server ingests for scan validation, tool identification, and future automation workflows.
Expanded collector toolset
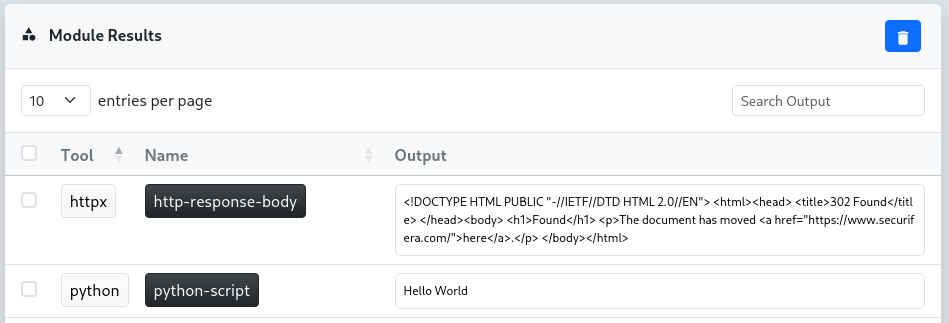
Over the past month, we added four new tools to the reverge collector project: gau, IIS short name scanner, webcap, and python. Each tool introduces unique functionality that expands the collector’s data-gathering capabilities.
gau
getallurls (gau) retrieves known URLs for a given domain from sources such as AlienVault’s Open Threat Exchange, the Wayback Machine, Common Crawl, and URLScan. Beyond endpoint enumeration, gau can help identify web technologies through returned file extensions and paths, seed wordlists for brute-forcing additional endpoints, and uncover other insights useful in reconnaissance.
IIS short name scanner
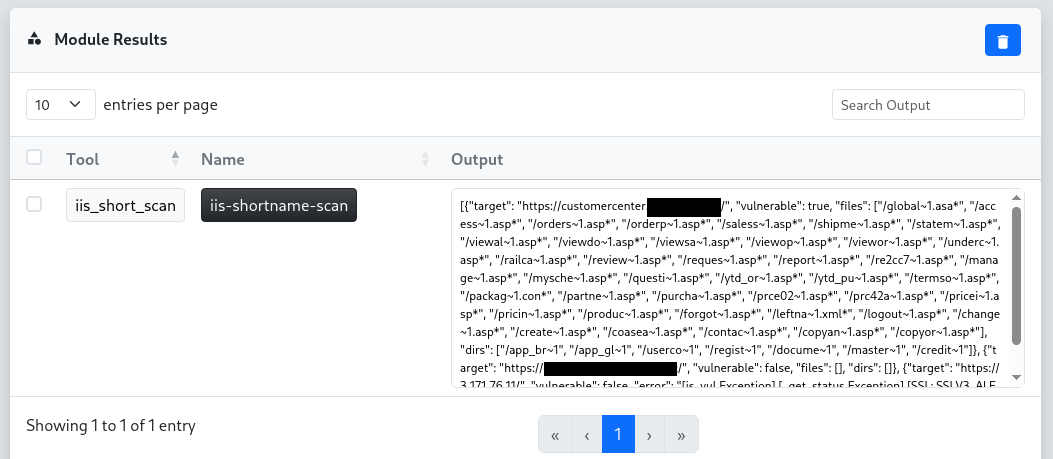
The IIS short file name disclosure scanner exploits a long-known vulnerability in Microsoft IIS where requests with a tilde (~) reveal short file and folder names. This can be extremely useful for web endpoint enumeration and assisted path/endpoint brute forcing.
webcap
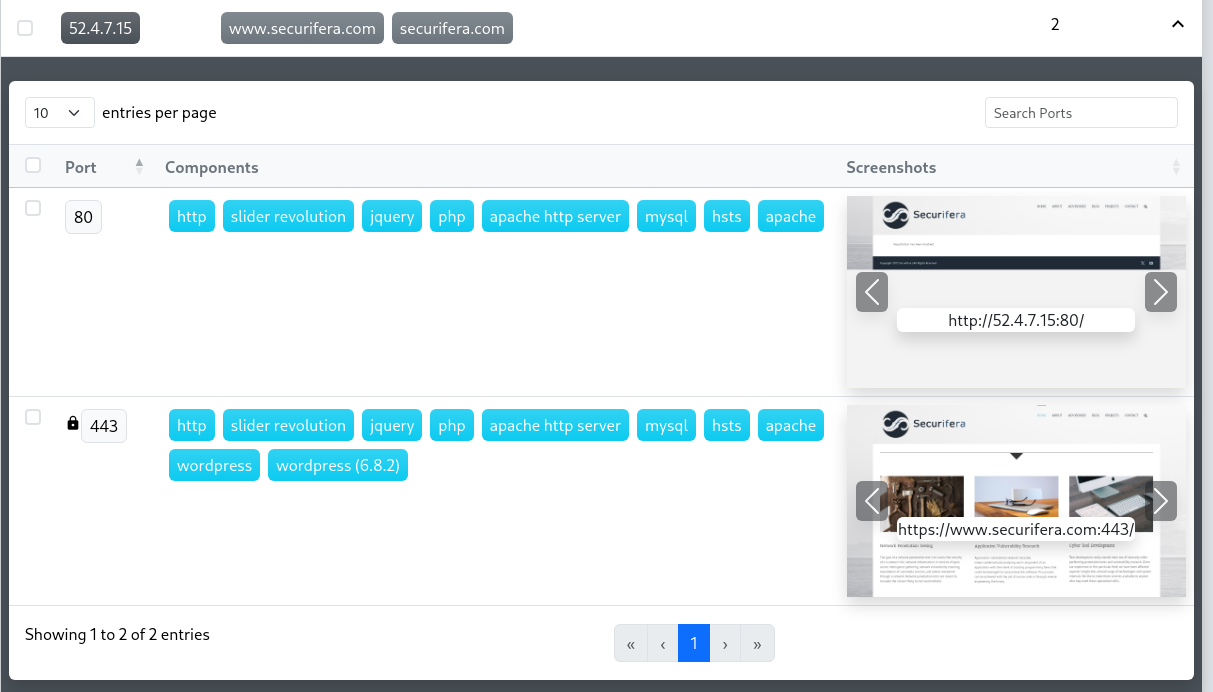
WebCap is a lightweight web screenshot utility that uses Chrome’s remote debugging to navigate to endpoints and capture screenshots. While Reverge previously included a custom tool called pyshot (built on PhantomJS) for this purpose, PhantomJS is now easily detected by Cloudflare, often preventing it from retrieving Cloudflare-served endpoints. WebCap addresses this limitation by relying on Chrome instead.
python
The python tool was introduced to enable future LLM-driven automation, providing a way to execute custom code dynamically once AI agent features are integrated.
With these new collector tools, reverge continues to broaden its data aggregation and security scanning capabilities. If you’re considering an attack surface management solution, or looking for an edge in pentests, red team operations, or bug bounty work, give reverge a try. You won’t be disappointed. Available exclusively on AWS Marketplace.