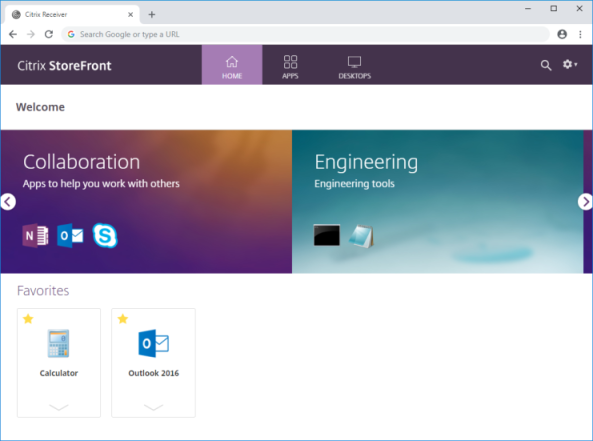
From POC to RCE with reverge
From POC to RCE with reverge Last month, Securifera publicly launched our attack surface management tool, reverge, on the AWS Marketplace. While we’re still planning to publish blog posts and videos to guide users through setup and usage, we wanted to give an example of what reverge can do by demonstrating how [...]