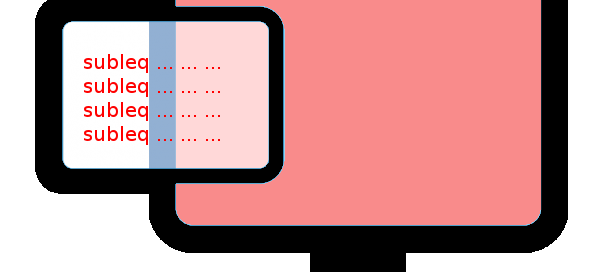
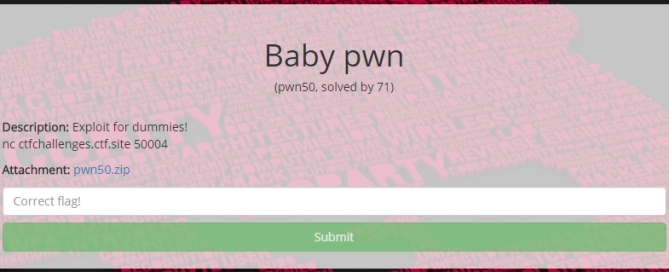
Defcon 2020 Red Team Village CTF – Seeding Part 1 & 2
Defcon 2020 Red Team CTF - Seeding Part 1 & 2 Last month was Defcon and with it came the usual rounds of competitions and CTFs. With work and family I didn't have a ton of time to dedicate to the Defcon CTF so I decided to check out the Red Team [...]