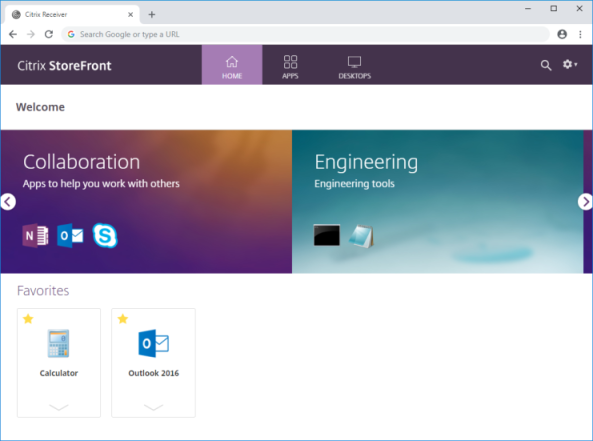
Hacking Citrix Storefront Users
This article is in no way affiliated, sponsored, or endorsed with/by Citrix Systems, Inc. All graphics are being displayed under fair use for the purposes of this article. Hacking Citrix Storefront Users With the substantial shift from traditional work environments to remote/telework capable infrastructures due to COVID-19, products like Citrix [...]